Cryptography & Cryptanalysis
密码学代写 Type your answers after the each question in this document using BLUEcolor fonts. You must explain all your answers and workings…
Instructions: 密码学代写
- Type your answers after the each question in this document using BLUEcolor fonts.
- You must explain all your answers and workings, otherwise you may not get any mark.
- Where required to display your work, capture and paste the relevant screen shots into your document.
________________________________________________________________________________
Question 1.
The following cipher text was sent from Bob to Alice using an XOR operation with an unknown 8-bit key. It is discovered that the 8-bit key has been repeated reused (i.e. not a OTP) which is a fatal mistake. It is also known that that plaintext is in English.
Assuming that the letter frequency distribution applies in this short message, use the frequency analysis attack to find the key and hence obtain the plaintext. (10 marks)
Cipher text: 11110000 11111001 11110000 11100011 11110000 11111011
Question 2. 密码学代写
Break the following ciphertext using the CrypTool2 “AES Analysis using Entropy 1” template.
Go to this website https://www.cryptool.org/en/ct2/ . Download and install CrypTool2 in your computer. Open CrypTool2, in Startcenter, Templates, select Cryptanalysis, Modern, AES Analysis Using Entropy (1).
For each case below, copy and past the following ciphertexts into “Text input” panel. On top panel clisk Stop. Then in “Key Searcher”, click on the “gear” symbol and enter the key below, then click Play.
(A). Ciphertext: (encrypted using AES 128 bit key, in ECB mode)
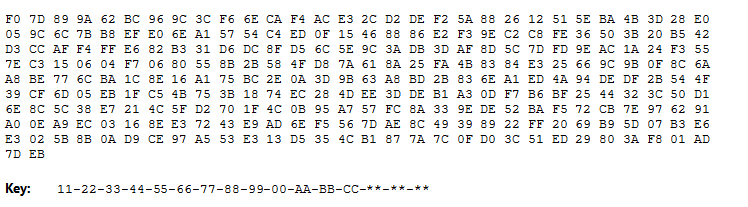
Questions:
- What is the plaintext Output
- Provide a readable screenshot
- How many possible keys are there if the key were:
**-**-FF-FF-FF-FF-FF-FF-FF-FF-FF-FF-FF-**-**-**
(8 marks)
(B). Same plaintext encrypted using AES 128 bit key, in CBC mode – (notice the first 16 bytes are the same as ECB mode)
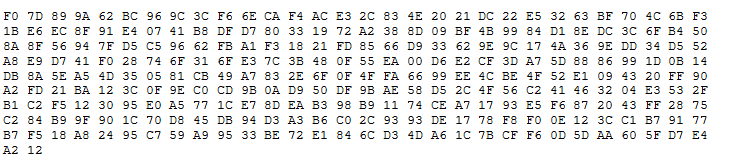
a.Is the entropy analysis able to obtain the plaintext? If not provide an explanation. (2 marks)
Question 3. 密码学代写
Perform the substitution attack on a cipher using DES ECB mode. Create two text files containing the following text.
alice.txt: ALICE WILL PAY: $90,000 TO ALEXANDER joyce.txt: JOYCE WILL PAY: $10,000 TO TIMOTHY
(i) Encrypt each file using DES-ECB mode with “-nosalt” using the same secret password to get two files alice.ecb, and jouce.ecb.
Display the the screen shot of the output hexdump. (5 marks)
$ openssl enc -des-ecb -nosalt -in alice.txt -out alice.ecb
(ii) Consider that an attacker is able obtain both ciphertexts. Demonstrate how the content of joyce.ecb can be change to “JOYCE WILL PAY: $90,000 TO TIMOTHY”.
You would need to use a hexeditor (e.g. hexcurse) to display the contents of the source ciphertext file and copy the relevant parts to the target ciphertext.
Screenshot the relevant hexeditor screen, showing how the forgery is done.
[Note: DES blocks are 64 bits. The above messages are constructed such that the target area in the ciphertext are exactly inside a block, making it easy to copy and paste in a hex editor. Otherwise it would require to attacker to manipulate the bits in the ciphertext.]
Would this attack work on these two files with other modes: des-cbc, des-ofb, des-cfb, des- ctr? (20 marks)
Question 4. 密码学代写
Compare the encryption of an image with a flat background using AES 128 in ECB and CBC modes. Choose one image (preferably bmp format), e.g. your ID photo which has a uniform flat background. Encrypt it using AES-ECB and AES-CBC modes.
Display the plaintext and encrypted images. Include the screen shots. (25 marks)




