Assignment 2 – Speakers
Speakers代写 In this report, two speaker lectures will be explained on how they were presented to address the information Assurance···
In this report, two speaker lectures will be explained on how they were presented to address the information Assurance, what they concluded and the tie with the course, as well as their comparison. The two speakers discussed are Mr. Dave Ratisher who gave a lecture on the Mueller election hacking report and Ms. Patricia, who is the IA expert at Apple Inc. and give a presentation on the information assurance and security. The purpose of this paper is to build the understanding of the IA issues as presented in both lectures and how they relate to the coursework.
Mr. Dave Ratisher Presentation Speakers代写
It was on a Tuesday, 27th in the evening when Dave Ratisher gave the talk on the alleged election and voting risk. The speaker mainly focused on Robert Mueller report on 12 Russian hacking of the DCCC and the Democratic campaign (Chang 2018). In the talk, he presented the risks that made the information assurance vulnerable to the attack. In essence, the issue was, what went wrong during the 2016 presidential campaigns and during the election and the risk which were pertinent to it. The speaker addressed on the issue in the dimensions of what happened and what could have been done to mitigate the information integrity issues.
The discussion of the Mueller report was important as it informed more of the issues of information assurance and how such information can be vulnerable from the attack if no proper caution measures are taken. The election hacking is a practical and perfect example of how even seemingly secure system can be vulnerable to the attacks, therefore, triggering a question on what about the smaller projects like a company information system? As the audience and the learning student of IA, the presentation was mind opening.
Mr. Dave used a practical approach to present his report. Speakers代写
To start with, he illustrated the five pillars that ensure security measures for information assurance according to the Department of Defense Cyber Security Model
i. Availability
ii. Integrity
iii. Authentication
iv. Confidentiality
v. Non-repudiation
Mr. Dave then proceeded to explain how the Russian hackers stole information from the Democrats using flow diagrams. In the diagrams is the FBI special counsel Robert Mueller’s indictment against the 12 hackers. It describes how they allegedly stole data from the DCCC and Democratic National Committee as well as from some member of the Hillary Clinton campaign.
The hacking of Clinton campaign started in March 2016 using email phishing. The email-phishing use scam emails which trick the user into giving sensitive information like passwords. One of the staff members allegedly fell into this trap and was requested to reset the email password. Another trick used excel file which when it opens it redirects the user to the Russian website as shown in figure 1.
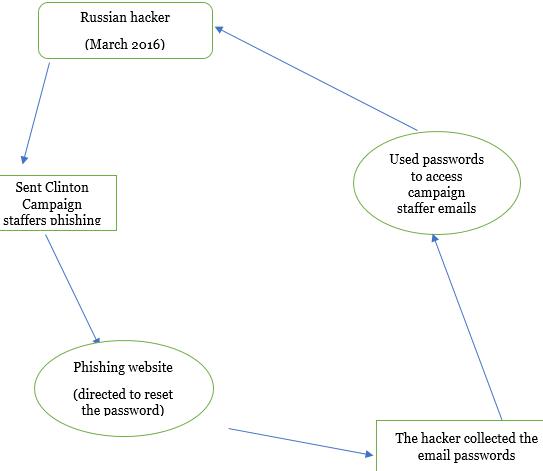
Figure 1: How Clinton campaign was hacked using email phishing
The speaker also explained how the DCCC and DNC were hacked as shown in figure 2. Speakers代写
The hacking took place in around 2016 when the Russian spy officers targeted DCCC and DNC. The attackers first gained privileges to the DCCC networks which they used to gather information to access the DNC networks. The Mueller report showed that the hackers installed X-agent malware in the group computers. The program gathered information using user activities through the keystrokes and the screen activity by taking screenshots. Through this effort, the hackers were able to harvest passwords, research on the opposition, internal communications, banking transactions and more.
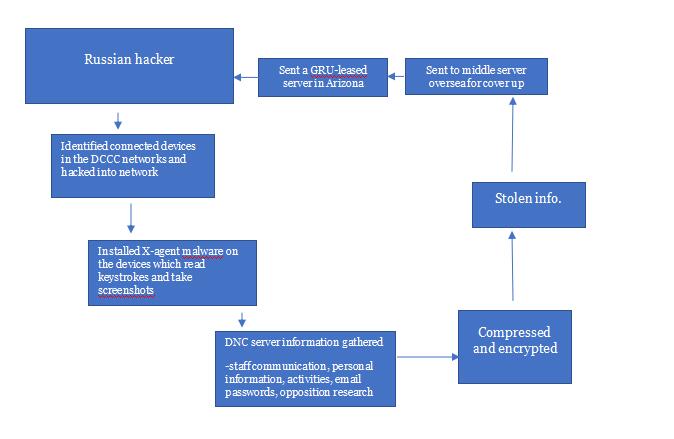
Figure 2: How DCCC and DNC were hacked by Russians
Ms. Patricia Presentation Speakers代写
The other speaker, Ms. Patricia, who was an IA specialist at Apple Inc. The lecture took place on Wednesday, 28th at the university hall. She attended for presentation in a CIS Graduate Seminar on the information assurance and cybersecurity. Here, the speaker addressed the increasing rate of cyber-attacks and system vulnerabilities in the organizations as well as individuals. The question that she raised was how we could ensure information security in our daily communications?
She used both scientific and descriptive approach in making her assertions. In so doing, she used the Facebook–Cambridge Analytica data scandal as a perfect example in explaining the information security and cybersecurity (Chang 2018). In the scandal, Facebook was probed for the integrity of their client data which was accessed by political campaign consultants in Cambridge Analytica.

Cambridge Analytica is a political and marketing consultant who mainly depend on the data mined from the third parties.
Being a data mining company, it had created accounts with Facebook which were used for purposes of user matching in their campaigns. What happened is that the company acquired 50 million Facebook user information without their consent. This was a breach of the Facebook privacy policy, and Facebook was liable for information leak to third parties without their knowledge. Subsequently, the accounts were later closed.
It is believed that that the data was provided to Cambridge Analytica by a researcher called Aleksander Kogan who operated a firm called Global Science Research. The GSR had personality questions on Facebook which were used to compile a psychological profile of the user. Although Facebook allowed, it had no control of over it uses. However, the data was used for other ways that are against privacy policy by handing it over to Cambridge Analytica. The data was then used to access other useful information which Facebook considered a breach of data security. Using this scenario, the speaker demonstrated the importance of organizations to have mechanisms of following up the information for assurance of their intended uses.
Comparison, Ties, and Application Speakers代写
Close analysis on both speakers, it was evident that information security has become a significant threat in today’s information assurance. They also seemed to agree on the critical components to ensuring data integrity which includes Availability, Integrity, Authentication, Confidentiality, and Non-repudiation (Infinit-o 2018). Therefore, organizations and information security experts have the responsibility to track of the network communication to ensure any breach is identified, analyzed and solved. According to the Mueller report on election risk, the worker needs to have specialized training on matters system and cyber security for them not to fall prey to hacking which may jeopardize the integrity of the whole organization.

The two lectures considerably inform on the classroom course through the real-world events regarding information assurance. They also offer in-depth insight into the current issues affecting information communication and how they can be controlled. Notably, the lectures illuminated more on the coursework regarding the data security and measures.
Conclusion
Information assurance has become a modern trend as it has been observed from the speaker’s perspectives. Therefore, individuals and organization must install mechanisms to detect and control information breach and leaks like the case of Facebook and DCCC as well as DNC hacking. To protect the system, the IA specialists need to use the modern methods of data encryptions, anti-malware, and firewalls. Above all, proper training of the employees on the matter of system security is also essential in IA security measures.
References Speakers代写
Chang, A. 2018. “The Facebook and Cambridge Analytica scandal explained with a simple diagram,” Vox, (available at https://www.vox.com/policy-and-politics/2018/3/23/17151916/facebook-cambridge-analytica-trump-diagram; retrieved November 28, 2018).
Chang, A. 2018. “How Russian hackers stole information from Democrats, in 3 simple diagrams”, Vox, (available at https://www.vox.com/policy-and-politics/2018/7/16/17575940/russian-election-hack-democrats-trump-putin-diagram; retrieved November 28, 2018).
Infinito. 2018. “The 5 Pillars of Information Security and How to Manage Them”, Infinito, (available at https://resourcecenter.infinit-o.com/blog/the-5-pillars-of-information-security-and-how-to-manage-them; retrieved November 28, 2018).
更多其他:Report代写 商科论文代写 代写论文 Essay代写 人文社科代写 Review代写 艾莎代写 Case study代写 研究论文代写 艺术论文代写 文学论文代写 心理学论文代写 哲学论文代写 cs论文代写 学术代写 cs代写



