CSE 523 – System Security
系统安全代写 Homework #5
系统安全代写 In this final assignment of the semester, you are asked to demonstrate your comprehensive understanding of the vulnerabilities…
Overview
In this final assignment of the semester, you are asked to demonstrate your comprehensive understanding of the vulnerabilities and exploit techniques we covered, as well as your ability to think as a security researcher and explore a given setup. Your final goal is to obtain the content of the “secret” file from the /root directory.
In order to do this, you will have to complete the following tasks:
- Obtainremote access to the victim VM by exploiting a service vulnerability
- Gainpersistent access by searching for important account information, that might have been exposed due to lack of security awareness.
- Discoverand exploit vulnerabilities of programs within the “Custom_Scripts” directory to gain root privilege
- Navigateto “/root” and screenshot the contents of the directory and the contents of the file “secret”
The given setup is presented in Figure 1.
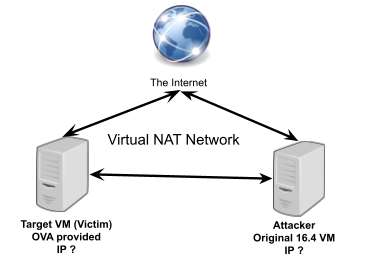
Figure 1. HW 5 setup
Download and CSE 523 – Final.ova as your target VM, and follow the instructions here to configure your network. Note that this configuration is different from the one we used in studio 10 and HW4, and relies on a NAT network instead of an internal network.
You are not given the machine password, so you won’t be able to access the victim machine directly. Keep in mind that guessing the password will not satisfy the objectives of the assignment, although you are welcome to try 🙂
Hints / Questions to ask yourself: 系统安全代写
- Obtainingaccess to the VM remotely
a.In order to communicate with a machine over the network, what must you know about that VM?
b.You do not know the password for any user accounts, how might you gain access to the machine?
c.What services are running on the machine?
i.Do those services have potential vulnerabilities?
2.Explorethe VM and Gain persistent access
a.How can you run arbitrary commands on the remote VM?
b.How can you search files for keywords?
c.Could some users store passwords in unsecured locations?
3.Discoverand exploit vulnerabilities
a.Do the programs accept input?
i.From the command line?
ii.From std input?
iii.From a file?
b.If so, can a user control what that input is?
c.Is the input easily controlled? If not, how might you learn more about the program to understand potential vulnerabilities?
Final Writeup 系统安全代写
Your write-up should consist of two parts.
Part 1: Summary
- An executive summary describing your findings. An executive summary should notexceed 1-2 paragraphs
- A full-screen screenshot showing the contents of the “/root” directory and the contents ofthe file “secret”. Please echo your name and date in this screenshot as you did in homework 4
Part 2: Reproducible notes 系统安全代写
- Aneat step-by-step walk-through of how you accomplished the Including
- All commands you ran
- An explanation of why you ran the command
- All Custom Code & Payloads
- Screenshots to assist with telling the story and showing us that you completedthe Specifically, you must include a full-screen screenshot showing each and every exploit command you ran and its output.
- A list of all Vulnerabilities exploited, why you chose to exploit them, & how you found the This can be a separate section, but you can also include this information in your step-by-step instructions.
NOTE: ALL content from the terminal that is documented in the writeup should be shown with screenshots and not copy & paste of text.
- Screenshotsshould be made with a snippet/screen capture tool on the computer and not taken with phones of your computer screen
- Yourreport should be consistently formatted and include structured You will lose points if we can’t follow your instructions due to bad formatting.
Generally, you should write the report in a way that you should be able to pick up your report a year from now and repeat the lab with ease.
Grading: 系统安全代写
You will be graded for correctness (successful exploitations) and for providing repeatable notes. You will lose points if we can’t follow your work, so showing the contents of /root and the secret file is not sufficient to get a perfect score.
You are to complete this final project on your own. Do not ask (or answer) questions of other students; do not discuss any aspect of this homework with any other student.
Direct all questions to the TAs and me. General questions that are not directly related to your approach/solution can (and should) be posted publicly on Piazza. 系统安全代写




